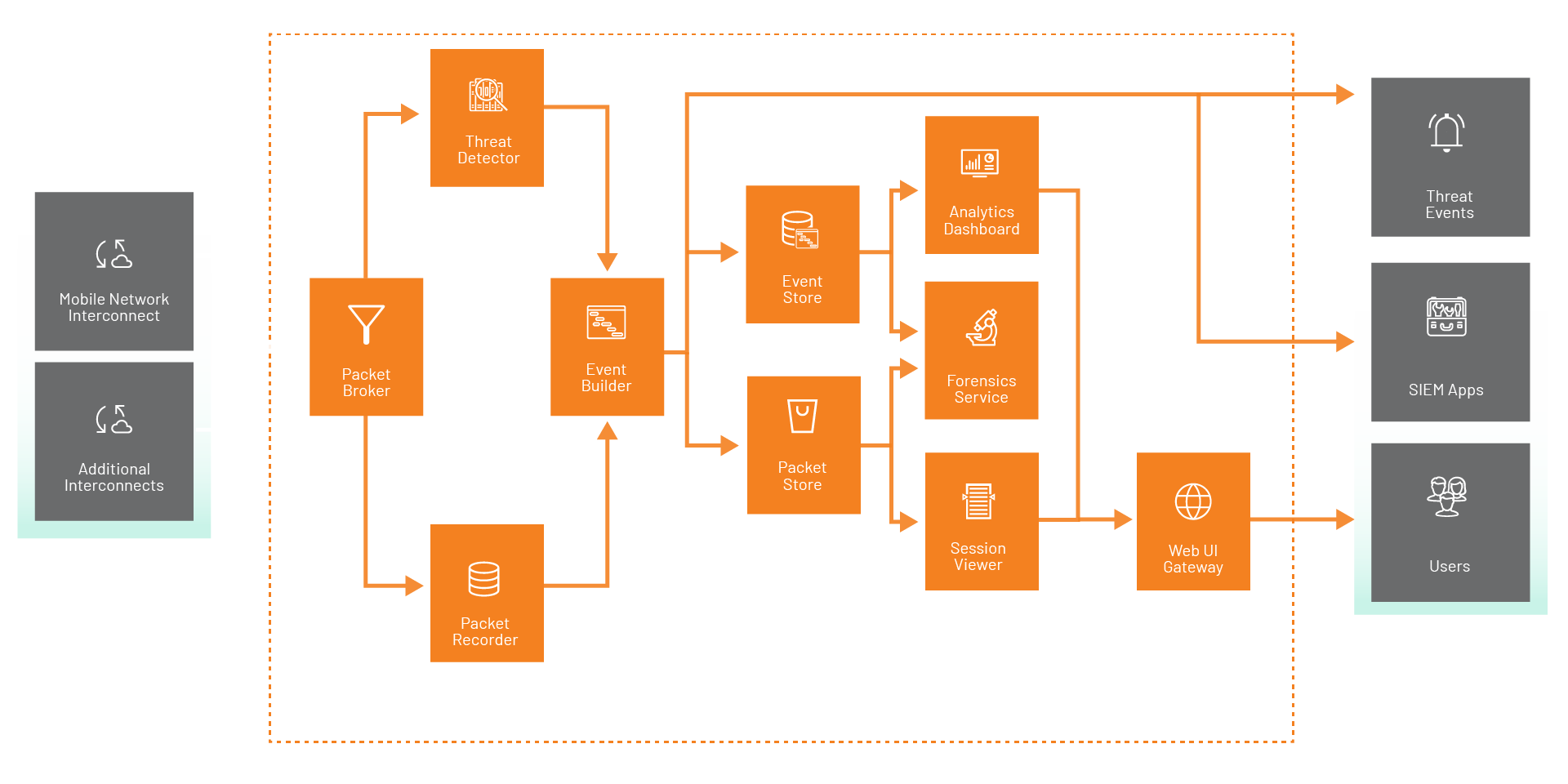
Vigilance Watchdog increases network security by intelligently comparing SS7 and Diameter traffic to known threat signatures and machine learning to spot unusual activity. Working alongside the existing firewalls, Watchdog records the packets before and after an event, creates a clear timeline, and provides your security team with the tools to analyze, understand, and take action quickly.
+1 (703) 659 9965
198 Van Buren Street, Suite 200
Herndon, Virginia 20170
United States of America
Apex 2, 1st Floor
97 Haymarket Terrace
Edinburgh EH12 5HD
United Kingdom